Monthly Archive:: August 2016
One of the most important things when writing an article represents choosing the right image, but you can’t have images for all can you? So if you don’t have images for all articles then where do you get images? Well one choice would be to get a paid subscription from some stock sites, but that
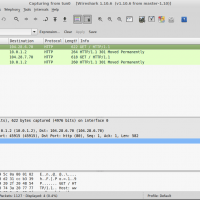
When connecting to public WiFi networks, such as those provided in airports or hotels you are limited to a specific time period and your access might be limited to specific sites only. At first sight there’s no way around this because the connection limitations will not allow you to do much and hacking it isn’t
I am going to start off with a series of link recommendations as what I find a good read needs to be shared: Documentation: Linux vs. FreeBSD (a case study) A praise for hackers The sad state of Romanian blogs The inventor that hacked the dictatorship 75% of Bluetooth smart locks can be hacked Apache
I kept seeing a lot of posts here and there throughout time across the p2p networks with cracked versions of WinRAR. These cracked versions contained basically a registry key and by the looks of it after all these years the developers behind WinRAR didn’t bother changing the algorithm to make the crack more difficult. And
While reading through my feed I came across a post from RedesZone which speaks about the latest release of BlackArch Linux. As it seems BlackArch is a pentesting distro built on top of Arch Linux and it’s main advantage is the bundle of over 1500 tools for security professionals. The complete list of tools can