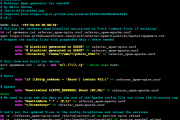
A new extortion method
I’ve been seeing reports from various people about a new type of extortion emails that are being received nowadays.
The emails in question threaten the victim with exposing it to the friends and family for watching porn or doing some other potentially incorrect activity online, like downloading torrents.
To draw the attention the blackmailers provide the victim with one of the passwords used and in most cases it is a very weak password.
Most victims admin that the password in question was either still used, but for a different email address or was used in the past. So the claims of the blackmailers are not fully accurate which led me to believe that I may know how they are actually finding their victims and building the extortion.
Over the past few years we’ve learned that nearly every major online service provider has suffered a data leak through which personal details of the users were exposed, including email addresses and associated password hashes.
NOTE: To check if any of your personal details were leaked just go to https://haveibeenpwned.com/.
Some of these databases were being sold for cheap on the DeepWeb and some of them even had most of the passwords cracked.
So my theory is that the folks behind this new extortion campaign have acquired such a database (or more) or have started cracking the hashes from these databases and have gotten their hands on one of the passwords that the victim was using or is still using for some accounts. Having the email address, the password that was associated with an online account at some time and probably the name of the victim is enough to carry out an extortion.
I’ve had my own email and password hash leaked through Tumblr and Taringa database leaks so I may some day receive an extortion email just as well, if they manage to crack my password.
But wait, there’s more. Most of the victims that I’ve heard about were targeted by threats of exposure of personal activity related to online porn watching, fapping and so on.
This makes me believe that there’s a bit more to this story than just a random database leak because I’m pretty sure that the victims are targeted because their emails appeared in a database leak associated with an adult site like Ashley Madison or Adult Friend Finder.

Unfortunately, at this point there’s no way to avoid or prevent such blackmailing campaigns, however if you fall victim to one just ignore the email received because it’s a fraud and nothing more.
Additionally, if you are targeted by such an elaborate extortion scheme you should reconsider the security of your online presence and start resetting the credentials of all your online accounts to ones that are secure and follow these guidelines:
- has at least 14 characters;
- has uppercase letters;
- has lowercase letters;
- has numbers;
- has symbols, such as ` ! ” ? $ ? % ^ & * ( ) _ – + = { [ } ] : ; @ ‘ ~ # | \ < , > . ? /
- is not like your previous passwords;
- is not your name;
- is not your login;
- is not your friend’s name;
- is not your family member’s name;
- is not a dictionary word;
- is not a common name;
- is not a keyboard pattern, such as qwerty, asdfghjkl, or 12345678.
Besides that you should always make sure that you are running licensed software and that security products are installed on all your devices and that their signature database is always up to date.