/security/ Archive
If you have not been hiding under a rock for the past few days you probably know that the Great Firewall of China was breached and about 500GB of data had been leaked. But that is not the fun part. The actual fun part was that the leak revealed that the technology behind GFW was
I’ve been seeing reports from various people about a new type of extortion emails that are being received nowadays. The emails in question threaten the victim with exposing it to the friends and family for watching porn or doing some other potentially incorrect activity online, like downloading torrents. To draw the attention the blackmailers provide
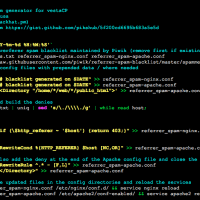
One of the nastiest problems when it comes to webserver resource and bandwidth usage is represented by the bad referrers which associate with a series of artificial queries from various hostnames that spam the crap out of the webserver and statistical logs. Because the accuracy of the statistical traffic reports is highly influenced by such
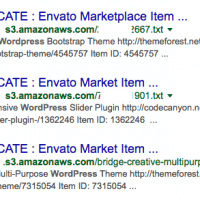
I’ve already covered a lot of stuff through the previous post, however there’s some stuff left to take into consideration. Stuff that’s commercial but offered for free elsewhere. First and foremost, if you do proper research you can get paid items for free. Let’s take the Lumieres theme for example which can be obtained here
A lot of folks have been praising a series of newly released apps and tools as well as online platforms and used words such as “secure” to describe them and reference them as bulletproof against eavesdropping. However all of them are meant to give a false feeling of security because every single app or platform is