[Tutorial] Greenbone Security Assistant + Let’s Encrypt
In the previous tutorial I included Certbot amongst the list of scripts that were to be installed on the server running OpenVAS and the Greenbone Security Assistant and I’m pretty sure that those who noticed it asked themselves why I did this. Well the answer is that I wanted to run the web interface of the Greenbone Security Assistant through a Let’s Encrypt certificate instead of a self-signed one.
Now, as you’ve probably seen already in the title of the post I did not refer to OpenVAS at all and I did this as it will continue to work on it’s self-signed certificates.
Assuming that you’ve followed my tutorial on setting up OpenVAS on Debian 9 in full I will pick up from where I left.
Before generating a SSL certificate from Let’s Encrypt we must first stop the Greenbone Security Assistant as Certbot will be using the same port and the certificate issuing would fail otherwise:
service greenbone-security-assistant stop
Now, assuming that you have a public hostname set correctly on your server and that this hostname is also set correctly at DNS level you can obtain the SSL certificate from Let’s Encrypt by running the following command:
certbot certonly
On the first prompt you must select the standalone server as Certbot will start a temporary webserver to verify the legitimacy of the request, generate the CSR and using it to generate the SSL certificate. Then you will be asked to fill in your email (so that you may receive expiration notices), to agree to the terms and also to fill in your hostname.
If everything is correct you should get your certificate and key generated under the /etc/letsencrypt/live/hostname/ directory. Obviously “hostname” is the hostname for which you’ve generated a SSL certificate.
Next to make the Greenbone Security Assistant use the newly generated certificate we must edit: /etc/systemd/system/greenbone-security-assistant.service and replace the following line:
ExecStart=/usr/local/sbin/gsad --foreground
with a line that includes the paths to the Let’s Encrypt certificate and key:
ExecStart=/usr/local/sbin/gsad --foreground --ssl-private-key=/etc/letsencrypt/live/hostname/privkey.pem --ssl-certificate=/etc/letsencrypt/live/hostname/cert.pem
Again, you must replace “hostname” with your own.
Because we made changes to a daemonized script we must run the following command to reload the scripts:
systemctl daemon-reload
And then just restart the Greenbone Security Assistant using:
service greenbone-security-assistant start
If all was done correctly you should be able to access the Greenbone Security Assistant through your browser and see that the SSL certificate used is valid: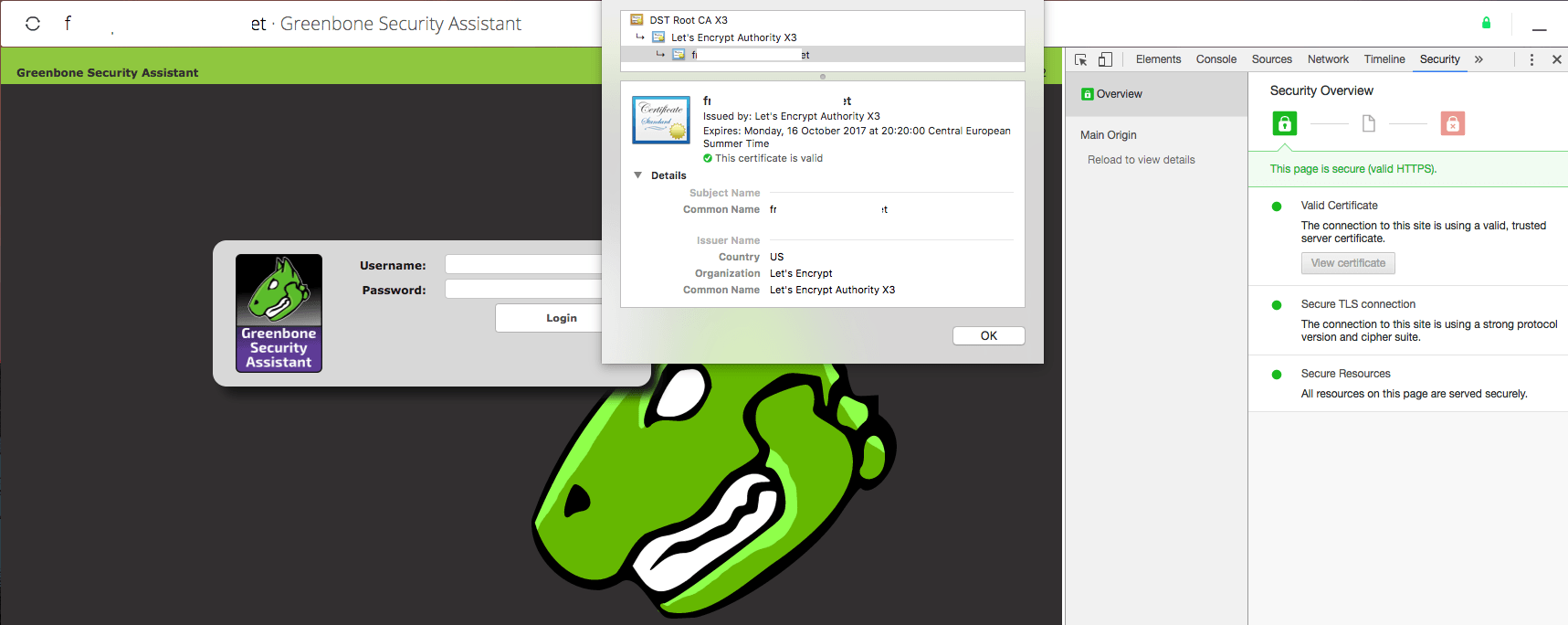 So far so good, however one problem still remains. The Let’s Encrypt certificate expires in 90 days and we should be getting it renewed automatically right?
So far so good, however one problem still remains. The Let’s Encrypt certificate expires in 90 days and we should be getting it renewed automatically right?
Well first and foremost we must create a log file for Certbot to write to so that we may have reference for any renewal failures or errors and we do that with this command:
touch /var/log/certbot.log
Once the log is created we must set a cronjob with the following commands:
* * 1 * * service greenbone-security-assistant stop && certbot renew >> /var/log/certbot.log && service greenbone-security-assistant start
This will stop the Greenbone Security Assistant service and attempt renewal on day 1 of each month and given the way Certbot is developed, if the certificate has less than 29 days to expiration it will renew it.
If for some reason the renewal fails you will receive a notification via email from Let’s Encrypt and should then check the /var/log/certbot.log to see why it failed.
With this out of the way, the only thing left for the OpenVAS install on Debian 9 is to find a way to compile the Samba plugin correctly. I’ll get back to that as soon as I get a chance and will issue another update.