/dev/null/ Archive
The newest TV series are full of bullshit when it comes to technology and the use of devices. For instance in NCSI Tim McGee was once doing traceroutes and directory listings under MSDOS and for the rest of the world he was “hacking” some other agency or a suspects PC. In CSI Cyber, probably the
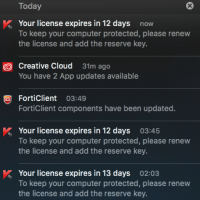
It’s no secret that IT security is a business, a profitable one for some major players, however this does not justify the need to apply intrusive expiration notices roughly two weeks before the expiration: Over the past 4 hours Kaspersky had sent me 3 notices already informing me that my license is going to expire
I wrote an article a while back on Securitate Informatica [RO] detailing how the exif data of a picture taken with a mobile device could expose the location and other sensitive data about someone and most importantly how risky all this information actually is. Unfortunately, these claims I made back then were proven justified as
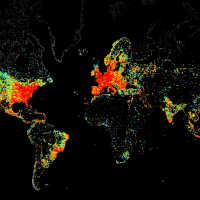
An imgur user created a map of all the devices connected to the internet by sending an ICMP Echo request, collecting the responses and mapping the active IPs using Python and here it is: The mind behind this map and the idea to make it is John Matherly, founder of the Shodan search engine and I must
The folks over at MyThemeShop.com (MTS) emailed a while back and announced their own bug bounty which aims to identify flaws in their website: In an effort to improve our user experience on our website and help our users better be able to find, preview and purchase new themes, we are announcing a new bug bounty program